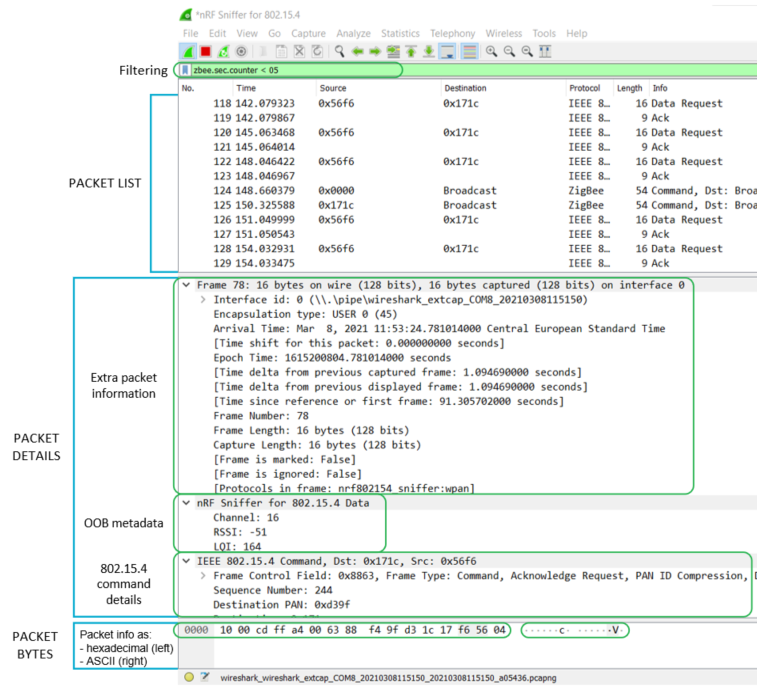
The nRF Sniffer passes all 802.15.4 packets to Wireshark, where they are wrapped in a header containing useful meta-information not present in the packet itself. Wireshark dissects the packets and separates the actual packet from the meta-information.
When you browse captured packets, select a packet in the packet
list to show the breakdown of that packet in the packet details
pane. The hexadecimal view of the packet is shown in the packet
bytes pane. Click a value in the details to highlight it among the bytes,
or click on the bytes to highlight it in the details.
Figure 1. Wireshark interface

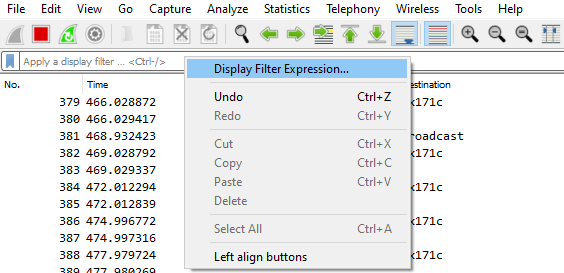
Use display filters to display a chosen packet subset. To open the filter menu
and construct a filter:
- Right-click the filtering bar.
- Click Display Filter Expression....
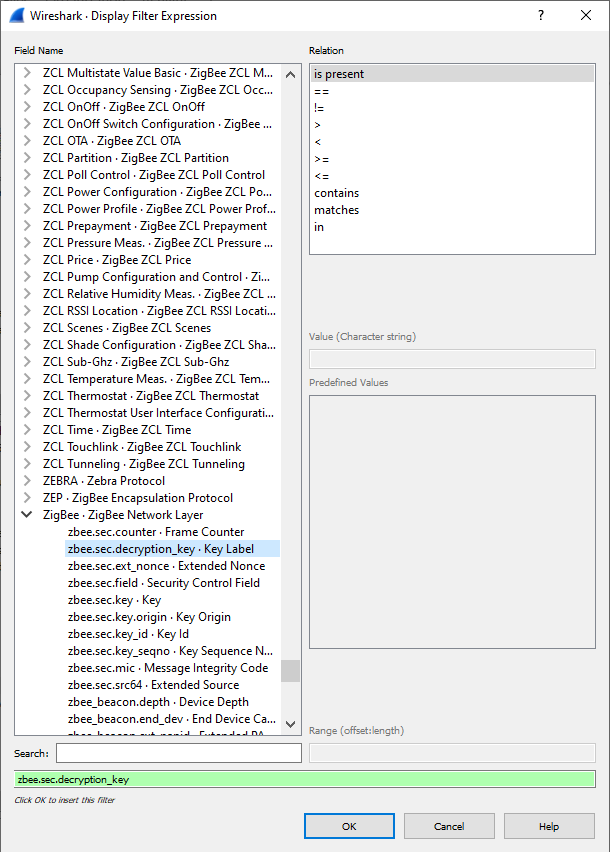
Most filters are based on the values of the packets, such as length or access
address. The filter expressions use Boolean operators (
&& || == !=
!). Figure 2. Wireshark interface for expressions

See the following table for some filter examples.
| Display filter | Description |
|---|---|
| wpan | Filter that displays all IEEE 802.15.4 traffic. |
| wpan.dst_pan | Filter that displays IEEE 802.15.4 packets that have a specific destination PAN. |
| wpan.dst16 | Filter that displays short destination addresses of IEEE 802.15.4 frames. |
| wpan.dst64 | Filter that displays long destination addresses of IEEE 802.15.4 frames. |
| wpan.src16 | Filter that displays short source addresses of IEEE 802.15.4 frames. |
| wpan.src64 | Filter that displays long source addresses of IEEE 802.15.4 frames. |
| ipv6, coap, dtls, udp | Examples of filters for packets that can be encountered on Thread and IP networks. |
| mle | Protocol filter that displays all Mesh Link Establishment traffic. Used for example by Thread. |
The following tips can help when inspecting your data:
See the documentation on the Wireshark website for more
information.